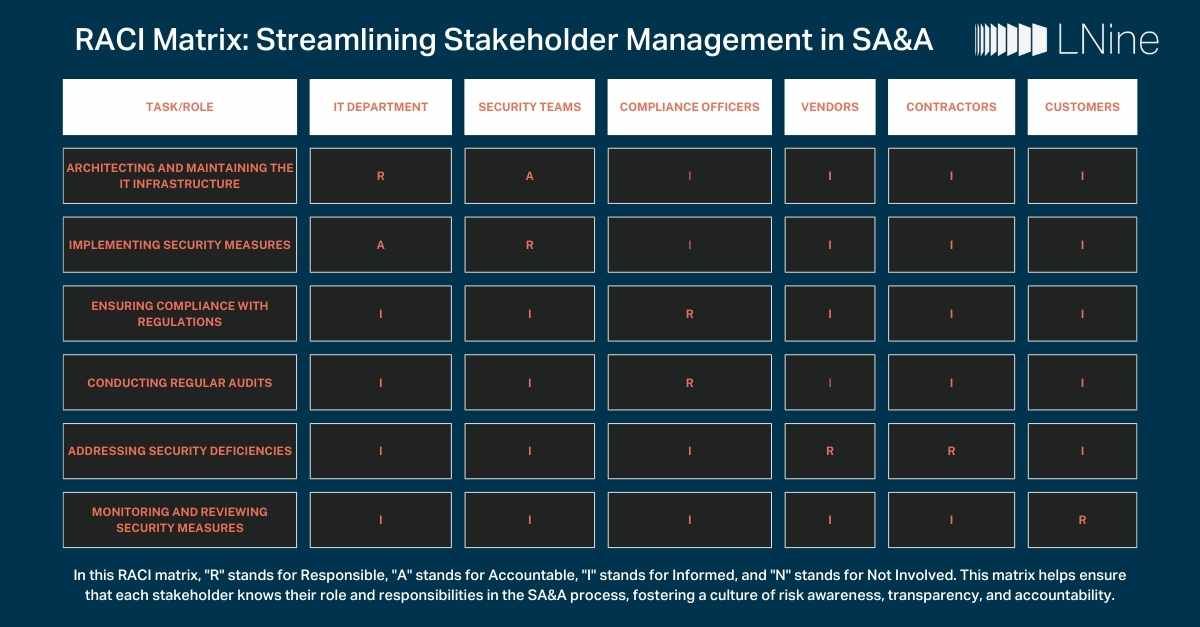
Introduction:
Government cloud transformation is more than just migrating workloads to the cloud; it's a fundamental shift in how organizations approach technology, security, and development. While compliance with regulations like FedRAMP, NIST, and ITSG-33 is essential, true security comes from embedding it into the very fabric of the development process. This blog explores the critical importance of fostering a culture of secure development, emphasizing how proactive security practices and continuous training contribute to building robust, compliant, and efficient government cloud environments.
The Limitations of Compliance-Driven Security:
Many organizations treat security as a checklist, focusing solely on meeting compliance requirements. While this approach is necessary, it often leads to a reactive security posture. Security vulnerabilities are discovered late in the development cycle, resulting in costly delays and potential breaches. To truly secure government cloud environments, organizations must move beyond compliance and embrace a proactive, culture-driven approach.
Building a Culture of Secure Development:
Creating a culture of secure development requires a holistic approach that involves people, processes, and technology.
Key Elements of a Secure Development Culture:
- Security Awareness and Training:
- Regular security awareness training for all development team members is essential.
- Training should cover secure coding practices, common vulnerabilities, and the latest security threats.
- Foster a culture of continuous learning, encouraging developers to stay up-to-date on security best practices.
- Shift-Left Security:
- Integrate security into every stage of the development lifecycle, from planning and design to testing and deployment.
- Embrace "shift-left" security principles, where security considerations are addressed early in the process.
- Implementing threat modeling early in the SDLC is key.
- Secure Coding Practices:
- Enforce secure coding standards and guidelines.
- Use static code analysis tools to identify potential vulnerabilities in code.
- Conduct regular code reviews to ensure adherence to secure coding practices.
- Automated Security Testing:
- Integrate security testing tools into the CI/CD pipeline.
- Automate security testing processes, including static analysis, dynamic analysis, and vulnerability scanning.
- Continuous monitoring of security posture.
- Security Champions:
- Designate security champions within development teams to promote security best practices.
- Security champions act as liaisons between development and security teams.
- They help to enforce policy, and educate their teams.
- Collaboration and Communication:
- Foster open communication and collaboration between development and security teams.
- Encourage developers to report potential security vulnerabilities.
- Create a blame-less environment where developers feel safe to report issues.
- Continuous Improvement:
- Regularly evaluate and improve security processes and practices.
- Conduct post-incident reviews to identify lessons learned and implement corrective actions.
- Regularly update security policies to adapt to the changing threat landscape.
The Benefits of a Secure Development Culture:
- Reduced Security Risks: Proactive security practices minimize the likelihood of security breaches.
- Improved Compliance: Embedding security into the development process streamlines compliance efforts.
- Increased Efficiency: Early detection and remediation of vulnerabilities reduce costly rework and delays.
- Enhanced Innovation: A secure foundation enables developers to innovate with confidence.
- Increased Trust: A strong security posture builds trust with government clients and stakeholders.
Government Cloud Transformation and Cultural Change:
Government cloud transformation requires a cultural shift that embraces security as a core value. Organizations must invest in training, tools, and processes that support a culture of secure development. By fostering a security-first mindset, organizations can build robust, compliant, and efficient government cloud environments.
Conclusion:
Moving beyond compliance and building a culture of secure development is essential for successful government cloud transformation. By prioritizing security at every stage of the development lifecycle, organizations can minimize risks, improve efficiency, and enhance innovation. This cultural shift not only protects sensitive government data but also builds trust and enables mission success.