Welcome to our 4-part blog series covering the intricate process of the Authority to Operate (ATO) and the key considerations for the Canadian government. In this series, we will dive into the details of how the ATO process works, its importance in fostering innovation and client services, and the challenges and opportunities it presents for the Canadian government. Stay tuned as we explore this complex and crucial topic in depth.
Latest Posts
- Cloud Transformation
- Modernization
- Authority to Operate
- cloud migration
- optimization
- Canadian Federal Government Contracting
- HIPAA
- Operational Excellence
- Security Assessment and Authorization
- Canadian Federal IT
- Cloud FinOps
- Cloud Management
- Cybersecurity
- Enterprise Architecture
- Information Management
- Canadian Federal Government employment
- Canadian Federal Government jobs
- Technical Debt
- Procurement Processes
- Technical debt in federal government
- Technical discussion
- AWS
- Canadian Federal Government resume
- Federal Government Staffing
- Microsoft
-
 Canadian Federal Government Contracting,
Operational Excellence,
Authority to Operate,
Cybersecurity,
Canadian Federal IT
Canadian Federal Government Contracting,
Operational Excellence,
Authority to Operate,
Cybersecurity,
Canadian Federal IT
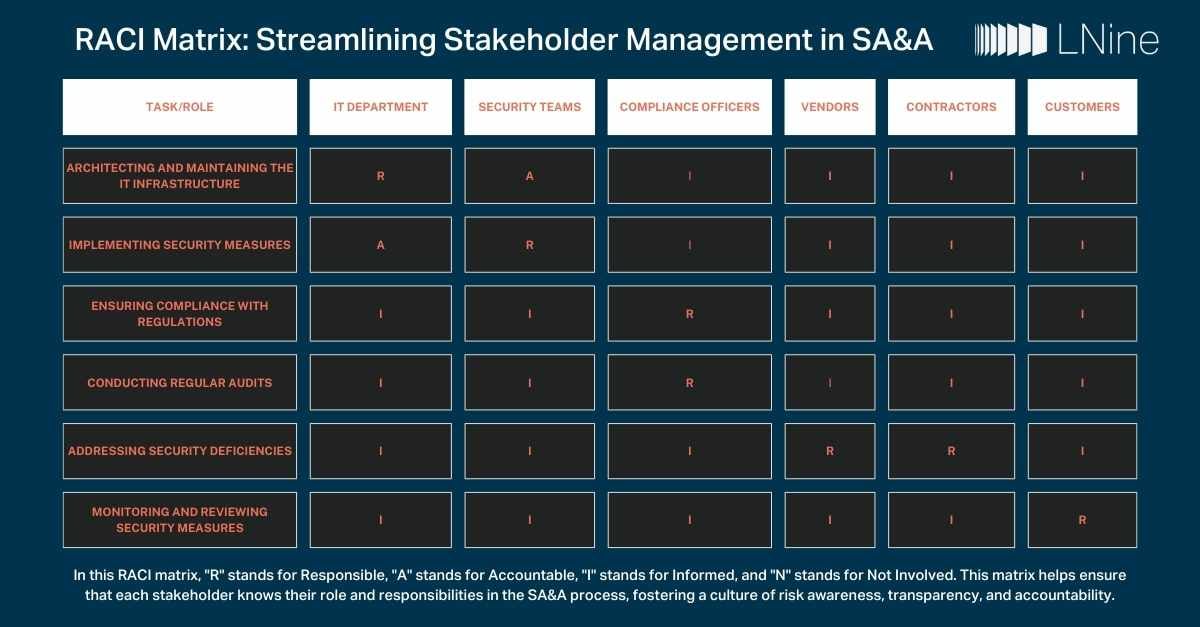
In the ever-evolving cybersecurity landscape, the Authorization to Operate (ATO) and Security Assessment and Authorization (SA&A) processes are the guardians of organizational resilience. At the forefront of these processes are primary and secondary stakeholders of the ATO and SA&A process, who orchestrate the delicate balance between functionality, fortification, and regulatory adherence.
In today's interconnected digital landscape, businesses face many security challenges. One crucial aspect of maintaining a robust security posture is Security Assessment and Authorization (SA&A). This process encompasses numerous factors, including proactive security measures, audits, data center consolidation, workload moves, and migration to the cloud.
The RACI matrix is a valuable tool for organizations to effectively manage the SA&A process, ensuring that all stakeholders are aligned and accountable for the security of the organization's digital assets.
In the dynamic landscape of cybersecurity, the Security Assessment and Authorization (SA&A) process is a crucial framework for organizations. Central to this process is the acceptance of risk, a delicate dance between security imperatives and business necessities. This blog post delves into the intricacies of risk acceptance within SA&A, offering insights into key considerations and practical approaches for businesses.
RECOMMENDATION
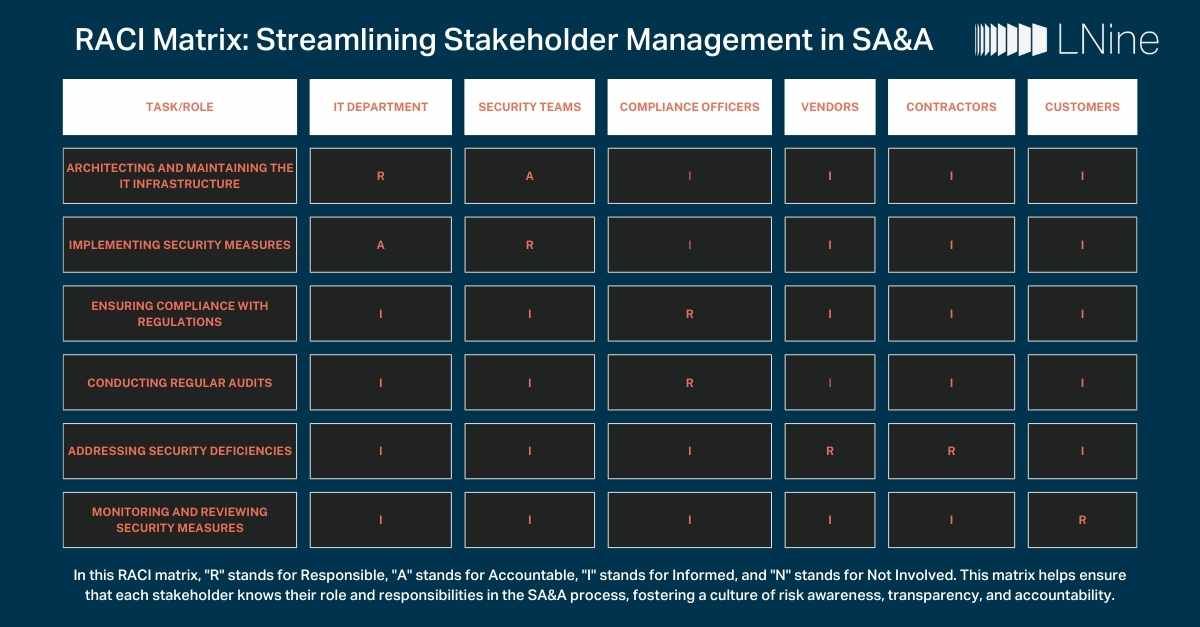
RACI Matrix: Streamlining Stakeholder Management in SA&A

From Risk to Resilience: Exploring ATO and SA&A in Modern Cybersecurity
Enterprise Architecture Journey: From Planning to Alignment