Enterprise Architecture (EA) can support and enable innovation within organizations by providing a structured approach to aligning business goals and objectives with technology solutions.
Latest Posts
- Cloud Transformation
- Modernization
- Authority to Operate
- cloud migration
- optimization
- Canadian Federal Government Contracting
- HIPAA
- Operational Excellence
- Security Assessment and Authorization
- Canadian Federal IT
- Cloud FinOps
- Cloud Management
- Cybersecurity
- Enterprise Architecture
- Information Management
- Canadian Federal Government employment
- Canadian Federal Government jobs
- Technical Debt
- Procurement Processes
- Technical debt in federal government
- Technical discussion
- AWS
- Canadian Federal Government resume
- Federal Government Staffing
- Microsoft
-
Recent Posts
In the ever-evolving cybersecurity landscape, the Authorization to Operate (ATO) and Security Assessment and Authorization (SA&A) processes are the guardians of organizational resilience. At the forefront of these processes are primary and secondary stakeholders of the ATO and SA&A process, who orchestrate the delicate balance between functionality, fortification, and regulatory adherence.
RECOMMENDATION
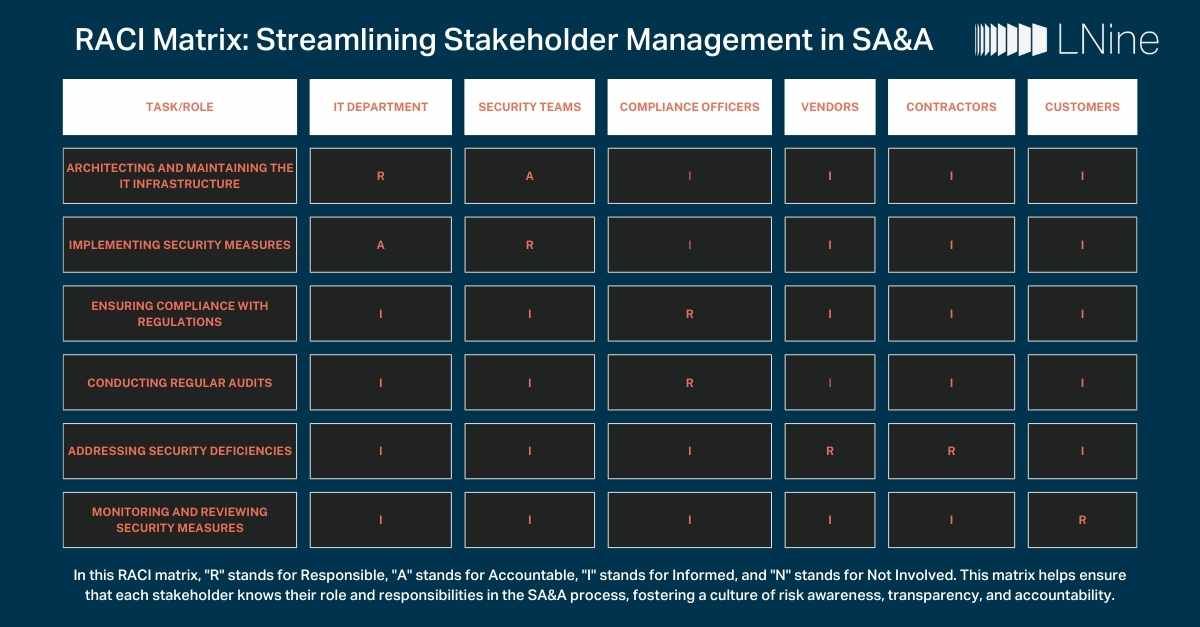
RACI Matrix: Streamlining Stakeholder Management in SA&A
The RACI matrix is a valuable tool for organizations to effectively manage the SA&A process, ensuring that all stakeholders are aligned and accountable for the security...

From Risk to Resilience: Exploring ATO and SA&A in Modern Cybersecurity
Welcome to our 4-part blog series covering the intricate process of the Authority to Operate (ATO) and the key considerations for the Canadian government. In this...
Enterprise Architecture Journey: From Planning to Alignment
Embarking on the EA journey requires careful planning and execution. Organizations must assess their readiness for EA adoption, establishing a cross-functional team that...

Optimizing Cloud Costs: Essential Skills for Cloud FinOps Specialists
If you think FinOps is solely about cost savings, it's time for a paradigm shift. At its core, FinOps is a wealth-building strategy that involves skillful management of...

